What is and how does steganography work?
3 July 2018 | Written by Filippo Scorza
It is an ancient and effective technique to hide messages between two interlocutors. Among the first users there was even King Demaratus and nowadays the potential of steganography has not escaped even Columbia University, which has developed a new system to use it.
It looks like a code word and, in fact, steganography is just that: a technique to hide a message between two interlocutors.
And it is not even a recent technique: already in 1500, it has been used to disguise and spread a treaty on cryptography in the form of a book on magic.
What is it? The message submitted with this technique appears to the reader in the form of an image, another text or a list that function as a “cover” of the source message. In essence, the original message is placed in a harmless container, which is usually referred to as “carrier”, of common use and which does not, at first sight, raise any kind of suspicion.
Steganography in history. In ancient Greece, Herodotus, tells how the Persian king Demaratus had used this system to concealing a message, by covering with simple wax the tables containing information on possible Persian invasions: in this way it would have been complicated to imagine the texts under the layer of wax.
Another example of the story reminds us of the tyrant of Miletus Istielus who, to instigate a revolt against the Persians, tattooed a message on the head of his most trusted servant, after shaving it, so that the message was completely invisible after the hair was regrown.
Other known examples of “physical steganography” concern the writing of messages with invisible inks, Morse code messages on woollen threads used to make garments or short messages covered later by the stamps.
But let’s see an example of computer steganography:
• we take an image, a jpeg of dimensions 1920×1080
• this image contains 2 million pixels
• we identify a series of insignificant pixels in this image
• we modify the value of these pixels by means of new brightness and/or colour values
• these new values represent the hidden content linked to the message we want to convey, perhaps related to the letters of the alphabet
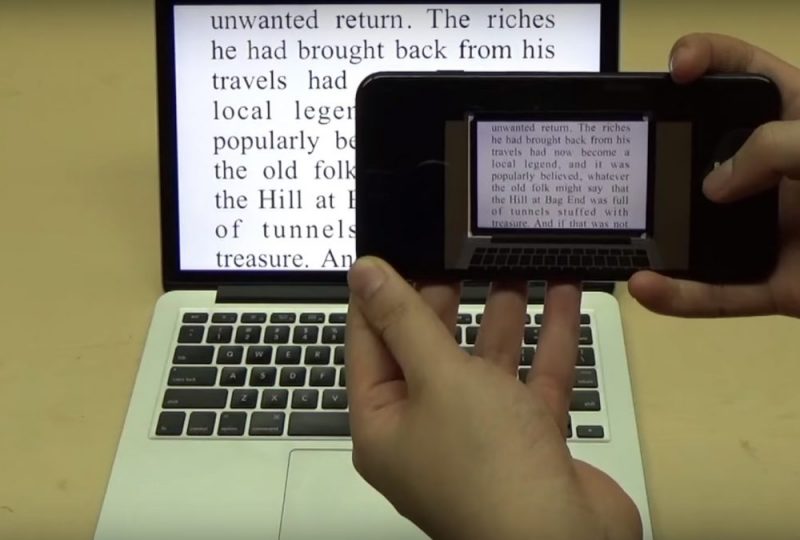
Another interesting technique of steganography is the “Fontcode” developed by Columbia University
Fontcode is based on the graphic modification of specific fonts in certain positions within the textual document; Thanks to a mobile application, it will be enough to frame the altered text to display the encoded message.
Fontcode could become not only a method of concealing information “top secret” but take space in more concrete applications, such as trademarking, anti-counterfeiting labels, symbols representing patents and guarantee system in favour of the authenticity of a document.
Surfing the net, however, it is not difficult to come across even “dangerous” declinations of this technology: it is the case, for example, of an extension of Google Chrome that allows anyone, even a terrorist, to use shorthand to convey messages encoded on any social network.
This application was carried out by a twenty-one-year-old, a student in computer science at Oxford University: the youngster declares that he did so to raise awareness to this method of transporting encrypted information.
As always, the technologies are neither good nor bad, it depends only on the use we make of them.





